In the ever-evolving landscape of cloud data platforms, Snowflake stands out as a powerful solution for data analytics. However, ensuring secure and efficient access to your data is paramount. In this blog post, we will delve into the practical challenges users often face when setting up network policies in Snowflake, exploring real-world examples and providing actionable solutions.
Overly Restrictive IP Whitelisting
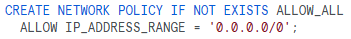
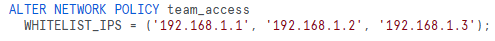
While setting up network policies organizations set up an IP whitelist, but due to frequent changes in users’ locations or the use of dynamic IPs, legitimate users find themselves locked out.
Consider using CIDR notation to specify ranges of IP addresses rather than listing individual IPs. This provides flexibility for users connecting from different locations or using dynamic IPs. For example:
Inadequate IP Blacklisting
An organization discovers suspicious activity from a particular IP address and decides to block it. However, they forget to regularly update the blacklist, leaving potential security gaps. In order to avoid this kind of problems companies need to Automate the process of blacklisting by leveraging Snowflake’s ability to execute SQL statements dynamically
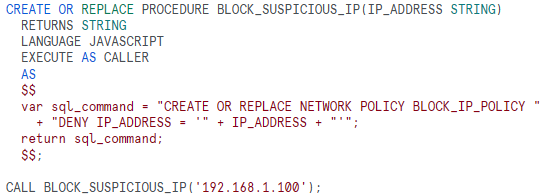
This procedure allows for dynamic updates to the blacklist, ensuring timely responses to potential threats.
Handling Network Policy Changes
When managing network policies in Snowflake, users often encounter challenges associated with making modifications to their policies. One common scenario involves unintentional or unexpected consequences that arise after implementing alterations to the network policy configuration. For example, unintended lockout and inability to revert changes are two of the primary issues users face.
To address the challenges outlined above, one effective solution is the use of stored procedures. Stored procedures in Snowflake allow users to encapsulate a series of SQL statements or other procedural logic, providing a way to automate tasks, handle exceptions, and facilitate easier management of network policy changes
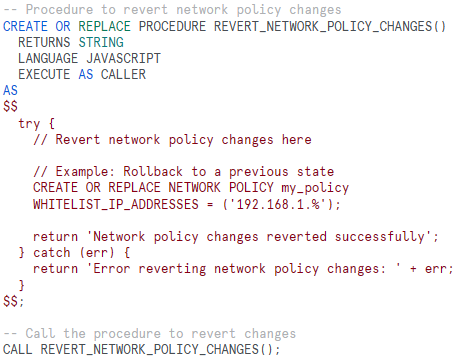
By incorporating stored procedures into the management of network policies, users can establish a more robust and automated approach to handle changes, mitigating the risks associated with unintended lockouts and difficulties in reverting modifications. This ensures a smoother and more controlled experience when managing network policies in Snowflake.
Locking Yourself Out
Imagine a scenario where you, as a conscientious Snowflake user, decide to fortify the security of your data environment by implementing a stringent network policy that blocks all IP addresses except your own. However, as the implications of your well-intentioned decision unfold, an unforeseen challenge emerges. Upon logging out of your Snowflake account, you suddenly realize the gravity of your actions – you’ve inadvertently locked yourself out of your own system, rendering it inaccessible. This situation arises from the fact that your network policy, intended to bolster security, has inadvertently become a barrier preventing your own access.
Avoiding the problems above, always have a backup plan or a secondary user with broader access. If you find yourself locked out, use another user to modify the network policy.
By adopting a proactive approach and maintaining alternative means of access, you can gracefully navigate the challenges posed by self-imposed lockouts and safeguard against unintentional disruptions to your workflow in the intricate landscape of Snowflake’s network policies. This approach exemplifies the importance of a holistic security strategy that not only seeks to fortify defenses but also anticipates and mitigates potential risks to maintain a seamless and secure data analytics environment.
Conclusion
Effective management of network policies in Snowflake is essential for creating a secure and collaborative data environment. By addressing common pitfalls with dynamic IP ranges, role-based policies, and granular controls, you can optimize your network configurations to match the dynamic needs of your organization. Remember, a well-designed network policy not only enhances security but also fosters seamless collaboration across borders and projects.
For more about “Network policies in Snowflake” refer to: Controlling network traffic with network policies | Snowflake Documentation
Read also my previous post: What makes Snowflake SQL outstanding from other DBMS (nimbusintelligence.com)





